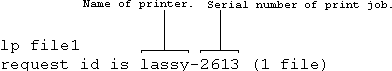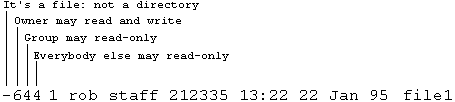Unix was written in 1972 by Kernighan & Ritchie at Bell Labs. It has since become the world's dominant operating system for both mainframe host machines and workstations. Its history is as follows:
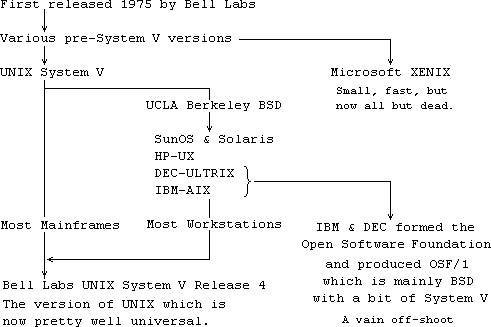
Despite the divergent routes of its development, the various versions of UNIX remained 75% identical. The divergent versions have now come back together again in System V Release 4. Check Login copyright note to see which version you are running. Nevertheless, some differences in commands remain between the System V and Berkeley BSD versions.
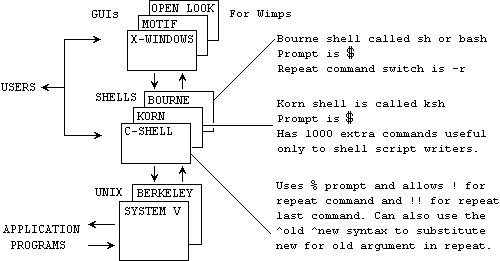
Whichever version of UNIX is used, it communicates with the user only through one of three shells (command processors) as shown below.
There are three main hardware set-ups through which you can use UNIX. A workstation contains something like a MIPS R4000 RISC processor and runs UNIX itself directly. A terminal merely gives you access to UNIX running on a UNIX host. A PC runs DOS which may be running a terminal emulator program directly or though Microsoft Windows.
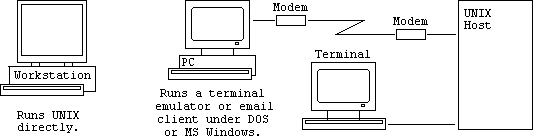
The local PC or terminal is connected to the UNIX host directly via a serial cable. A remote PC or terminal is normally connected only when necessary via a dial-up telephone line.
When you switch on your workstation it can take UNIX 10 to 15 minutes to initialise itself before it is ready to use. When you switch on a terminal or dial up from a PC, you may have to keep pressing Return, Ctrl-C, Ctrl-Z or Break to give the host a chance to lock on to your terminal's line-speed.
UNIX first displays your terminal id and then asks you to enter your Username and Password. When logging in, the # key effectively deletes the previous character. UNIX then displays its version details and then the prompt:
| % | for the C-shell and
|
|---|
| $ | for the Bourne or Korn shells
|
|---|
To change your password you type passwd. It then asks you to enter your current password and then your new password twice. To see what files you have, you type ls. You will then see a list of the files in your home directory. When typing in commands you can use:
| !! or r
| to repeat last command (!! C-shell, r Korn shell)
|
| Del, #, Ctrl-H
| to backspace over the previous character
|
| Ctrl-U or @
| to cancel current unfinished command line
|
| logout, exit, ^C
| to log out of UNIX and terminate your session
|
UNIX file names may be any length, but 14 characters is a sensible maximum. It is best to keep to letters and numbers, but file names can include any characters except:
/ ! @ # $ ^ & * ~ ( ) + ' " \ | ? < > space
These characters have special significance within UNIX commands. File names can be built of parts joined by dots, hyphens or underlines.
E.g. robs.new.book, flight-nav-prog, draft_accounts_1995.
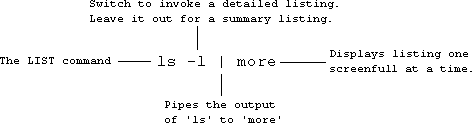
The following command lists the files in your current directory:
The following command copies file1 to file2 in the current directory.

If you do a cp copy without the -i, and file2 already exists, it gets overwritten and all the original contents are destroyed.
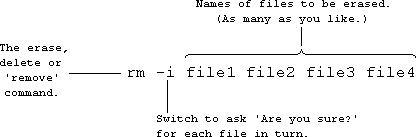
To erase files:
To change the name of a file in your current directory:
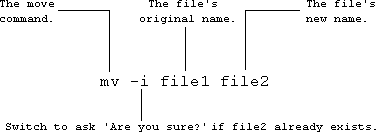
If you omit the -i and file2 already exists, its original contents are blown away.
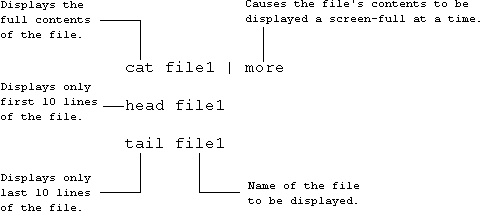
The following commands display the contents of a file on the screen.
The following commands print the contents of a file on the printer.
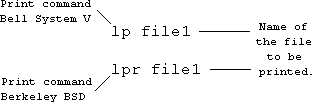
You have to have permission to use the printer. This is granted by the System Administrator.
The UNIX directory structure pertains to the computer as a whole: not just to a single disk drive. It starts with the root directory which is on the first disk drive. However, other disk drives start at what are called mount points which can be equated to any sub-directory. One of the directories within the root is called 'home'. It contains a sub-directory for each user, e.g.:
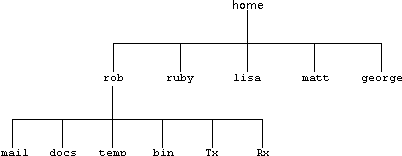
Each user's 'home' directory contains at least one sub-directory for his incoming email, one for his document files, one for temporary files and one for his executable files (programs). There will be others.
When you log in, UNIX automatically puts you in your home directory. You can create, edit or delete any file or sub-directories within your home directory or any of its sub-directories. But you cannot do so in anybody else's home directory without their permission.
| cd | transfers you to your home directory
|
|---|
| cd mail | transfer you to your mail directory
|
|---|
| cd .. | transfer to the parent of the current directory
|
|---|
| pwd | displays the current working directory
|
|---|
| mkdir source | make sub-directory called 'source' in current directory
|
|---|
| rmdir source | kill the source directory within current directory
|
|---|
| ls | list contents of current directory
|
|---|
| ls source | list the files in the source directory
|
|---|
| ls .. | list the contents of the current directory's parent
|
|---|
| mv dir1 dir2 | if dir2 does not exist, renames dir1 to dir2, but if it does, creates dir1 as a sub-directory of dir2
|
|---|
| ls file1
| by listing the directory you think it is in
|
|---|
| ls */file1
| by listing all sub-directories of current directory
|
|---|
or by using the find command:
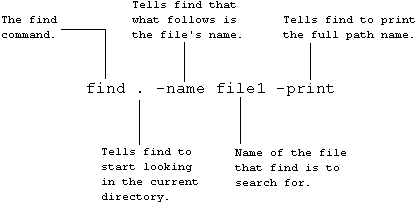
If you do not type the -print switch, find will say nothing, even if it finds the file you are looking for.
The find command searches for file names.
The grep command searches for strings within files.
Wildcard Characters
? is the wildcard substitute for any single character in a file name
* is the wildcard representing a string of characters of any length
| ls ?? | lists all files with two-character names
|
|---|
| ls c* | lists all files whose names begin with c
|
|---|
| rm f*ed | deletes all files whose names begin with f and end with ed
|
|---|
UNIX allows you to re-direct the output of a process from the normal standard output device to another destination such as a printer or a file:

You can also redirect a process's input source. Instead of letting it assume that it should get its input from the normal console keyboard, you can tell it to get its input from another terminal, a file or an input port:

You can also pipe the output of a process directly to another without storing the data in an intermediate file. The most common uses of the pipe are as follows:
| ls | more | feed directory listing one screen-full at a time
|
|---|
| ls | lp | send directory listing to printer instead of screen
|
|---|
You can also pipe the output of an initial process through more than one intermediate process before outputting the result. Intermediate processes are referred to as filters. An example of a filter is the sort process:
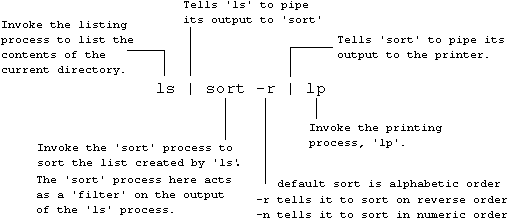
A UNIX system can have a number of printers. You may have a little HP Deskjet connected directly to your workstation. Your workstation may be networked to a UNIX host which has a heavy-duty line-printer and a large laser printer.

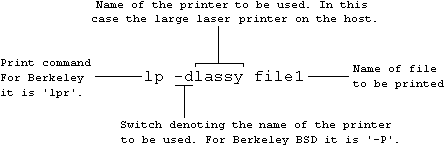
In UNIX, you give your printers names. You could call your little HP Deskjet printer 'jet'. The host's large line printer could be called 'bigboy'. The laser could be called 'lassy'.
When you configure UNIX on your machine, you specify which printer is going to be your default printer. It does not have to be the one that is connected directly to your machine. Your machine may not have one. When you do not specify any printer, UNIX uses your default printer. Otherwise when you give a print command you specify the printer to be used as follows:
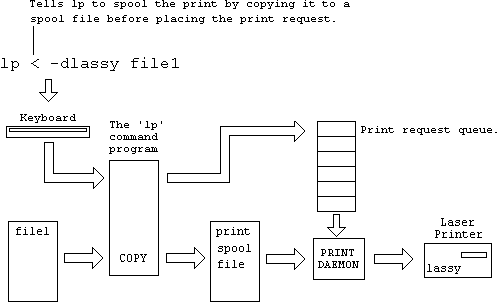
When you use the lp command to print something, it does not actually do the printing itself. It merely creates a print request which it puts on UNIX's print request queue. A print daemon deep within UNIX then handles the print requests in turn from the queue and performs the actual printing task as shown below.

This means that a lot of users on different terminals can each submit print requests to the same printer at the same time and they get put on the queue to be carried out in order without getting mixed up.
When you issue a print request such as lp file1, UNIX confirms your request by giving it a job number which it displays as follows.
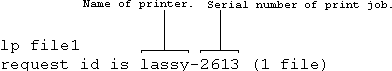
This allows you to identify the job later if anything goes wrong and you have to try to find out what has happened to it.
The lp command prints straight from the original file file1. So if after having placed the print request, you delete file1 before the print daemon has got around to printing it, the daemon will not be able to find it. To avoid this, you can tell the lp command to copy it to a print spool file first before putting the print request on the queue as follows.
The Berkeley command lpr spools print automatically. To stop it doing so type lpr -s file1. Useful for big files as spooling takes extra time and disk space which you may not have. Berkeley also has the facility to print-then-delete a file, lpr -r file1. So to print-then-delete a large file you type lpr -s -r file1.
BERKELEY BSD lpr only:
-s suppress the automatic spooling of your file before printing
-r automatically erase your actual file after having printed it
System V Printer Status Report
You can get the status of all the printers that are accessible to you as follows:
lpstat -a all
bigboy | accepting requests since 13:43:50 Thu 25 Apr 1991
|
jet | accepting requests since 10:20:13 Fri 12 May 1993
|
lassy | accepting requests since 09:15:22 Mon 19 Jun 1994
|
The report tells you when each printer was installed and put on-line. For an individual printer, you type its name:
lpstat -a jet
jet accepting requests since 10:20:13 Fri 12 May 1993
If you type lpstat without any arguments you get the current status of each print request on the print queue as follows:

System V - To Cancel a Print Request
To cancel this print request by removing it from the print queue and stopping any more of it being printed if it is already being printed, type:
cancel lassy-2620
request "lassy-2620" cancelled
If you want to cancel all the pending jobs on a given printer, type:
cancel lassy
NOTE: If the printer has an internal buffer, a lot of the file may still be in the buffer when you cancel the request. The printer may therefore carry on printing for 20 pages or more unless you clear or reset the printer's internal buffer.
Berkeley Printer Status Report
The equivalent printer status command and its associated report are:
lpq -a
bigboy:
|
Rank | Owner | Job | Files | Total Size
|
1st | eustace | 7 | file1 | 4615 bytes
|
lassy:
|
Rank | Owner | Job | Files | Total Size
|
2nd | eustace | 23 | file2 | 250327 bytes
|
jet:
|
Rank | Owner | Job | Files | Total Size
|
3rd | sharon | 12 | email | 1438 bytes
|
To get the current status of only those printers which are currently active or have requests pending in their queues, type lpq on its own.
To cancel a print request you refer to it by its job number, in this case 23 as follows:
lprm 23
Berkeley BSD responds with some utter gibberish that only a UNIX guru can understand.
Print Formatting Command
UNIX provides the pr command to format plain text files into titled pages as they are being passed for printing. The syntax and switches for the pr command are as follows:

pr can also print the contents of two or more files side-by-side in columns:
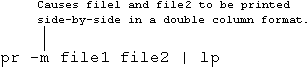
| cmp file1 file2
|
Compares the contents of two files. Says whether or not the two files are identical. Useful for getting rid of unwanted duplicates and for verifying that a file that has been there and back to a distant host is identical to the original and therefore arrived at the other end intact. Works for both text and binary files.
|
| diff file1 file2
|
Compares the contents of two text files. Shows lines that are different or have been added to one of the files.
|
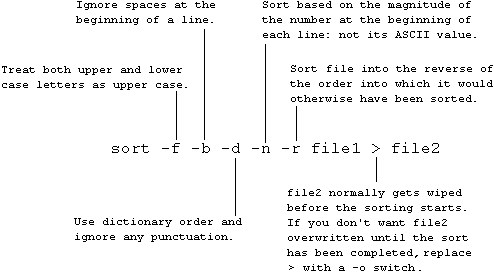
| sort file1 > file2
|
Sorts the contents of 'file1' into ASCII order and places them in 'file2'. Sort clears any previous version of 'file2' before starting the sort.
|
The full switch options for sort are as follows:
date
3:20 pm Thu 20 Jul 1995
| at 2:45 am | at 2:45 tomorrow morning
|
|---|
| sort -r hugefile -o hugesort | sort a huge file in reverse order
|
|---|
| pr -f -2 hugesort | lp | then format it and print it
|
|---|
| Ctrl-D | puts above script into scheduler
|
|---|
Console responses are place in a log file which appears in the user's email file the next morning.
If you maintain a text file called 'calendar' in your home directory in which you enter important events prefixed by their dates, then every midnight UNIX will send you an email message the next morning showing the events for the coming day and the day after.
| cal 7 1995 | displays calendar for given month and year.
|
|---|
| sleep 600; lp bigfile | start to print bigfile in one hour's time.
|
|---|
File Compression
To save on disk space, files which are referred to only occasionally can be compressed. Compressing files before transmitting them over a slow Internet link can also save on transmission time. To compress a file you use the 'compress' command as follows:
compress -v file1
file1: Compression 49.79%-replaced with file1.Z
The response is invoked by the -v switch. If you leave it out you get no message. You usually get a 50% saving with text files, but on some binary files you may not get any saving at all. To get 'file1' back you type:
uncompress file1.Z
You can read a compressed file directly without uncompressing it by using 'zcat' as follows:
zcat file1.Z | more
An older program called 'pack' uses a different compression algorithm from 'compress'. Although compress is generally better, 'pack' can work better than 'compress' on some files. It is therefore a good idea to try both to see which one gives the greater amount of compression.
File Contents
The file command tries to make a guess as to the kind of information a file contains:
file *
file1: data
file2: [nt]roff, tbl, or eqn input text
file3: ASCII text
file4.Z: compressed file-with 16 bits
It reckons 'file2' contains text which has been coded for input to the text formatter program troff. It reckons 'file4.Z' has been compressed according to a 16-bit compression scheme. 'uncompress' can uncompressed files which were compressed by any known compression scheme.
A Command Line Calculator
| bc | invoke the calculator
|
|---|
| (2+9)*3 | enter the expression you want evaluated
|
|---|
| 33 | bc puts the answer on the next line
|
|---|
| Ctrl-D | to leave the bc calculator.
|
|---|
A Banner Generator
banner "My Ultimate" "Program Listing"
Prints a tacky (in this case, two-line) banner heading in # marks.
When you type in a non-internal command on the command line, the UNIX shell looks for the executable file in your bin directory which is a sub-directory of your home directory. To get the programs there in the first place you can either copy them there with cp or move them there with mv:
To be able to run a program, you first have to make it an executable file as follows:
chmod -x newprogram
| designate the file as executable
|
rehash
| update the shell's hash table
|
When the shell starts up, it searches all the 'executable paths' for all the executable files on the system. It builds a list of all these executable files in what is called its hash table. The rehash command adds the new program to this table. The next time the shell starts up this new program will be put into the hash table automatically.
However, for this to work, there must be a path command in the .login file pointing to your own bin directory. If you are a new user, this might not have been done. To set a search path to your own bin directory, enter:

If you are using the Bourne or Korn shells, the path command is:
PATH=$PATH:HOME/bin
export PATH
You must add this to the .profile file in the case of Borne & Korn.
Shell Script Arguments
If you create a horrendous command with lots of arguments, to save on typing each time you use it, you put it in a shell script — perhaps along with other horrendously complex commands. UNIX allows you to pass arguments to these horrendously complex commands from the shell script command itself as follows:
Suppose you have the command:
pr -f -2 file1 file2 file3 | lp
You can put this in a shell script called 2print in the form:
pr -f -2 $* | lp
Then you can perform the same thing by typing:
2print file1 file2 file3
The file name arguments file1 file2 and file3 are visible within the script file as $1, $2 and $3. The internal argument $* therefore refers to each of them in turn. The arguments do not have to be file names. Whatever they are, the first argument on the script's command line is visible to commands inside the script as $1, the second as $2 and the third as $3 and so on.
To Run Another User's Program
To run a program called prog1 in Ruby's bin directory, type:
~ruby/bin/prog1 | for the C-shell
|
|---|
/home/ruby/bin/prog1 | for the Borne or Korn shells
|
|---|
If you want to use this program a lot, you can make it appear to be in your directory under a different name. You use the link command ln from your home directory as follows:
ln ~ruby/bin/prog1 bin/ruby1
You can then run the program any time thereafter by typing:
ruby1
If later, Ruby deletes her file prog1, her program ruby1 will still be in your directory.
To be able to set up such a link, both your stuff and Ruby's stuff must be on the same disk. If it is not, you can only set up a soft link adding the -s switch as follows:
ln -s ~ruby/bin/prog1 bin/ruby1
rehash
Everything works the same except that if Ruby deletes her program, you lose it too and the file name ruby1 points to limbo. You must delete the name using rm.
Using an Alias
You can create an short alias for a long command as follows:
alias ruby1 '/home/ruby/bin/prog1' | C-shell
|
|---|
alias ruby1='/home/ruby/bin/prog1' | Korn Shell
|
|---|
You can alias any command you like, e.g.:
alias sortnprint 'sort -r bigfile | pr -2 | lp'
To make alias commands permanent, you have to put them in the .login file or the .profile file.
Using a Shell Script
You can alternatively make a shell script called ruby1 in which you place the command line:
/home/ruby/bin/prog1
You then make it executable and add it to the hash table by typing:
chmod -x ruby1
rehash
You can then run Ruby's program by typing ruby1.
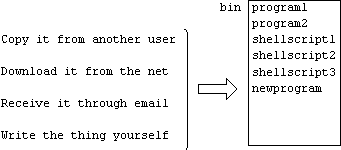
Getting Programs off The Internet
You can acquire programs from places on the Internet
Save the incoming email message in a file called something like received.shar.file.
Use a text editor to delete all lines up to the first line that begins with a #.
Feed the file to the shell by typing the command:
sh received.shar.file
The shell then unbundles the shar file into one or more other files. Some may be normal text files. Some may be uuencoded binary files. A program will at this stage be a uuencoded file called something like ruby1.uu. It will begin something like:
begin 775 ruby1
nhvr%$%()&)&_*&_s/Cxyn;idigbijiy#
gbosserygutigpto#hbypkikypiknbda
To get the executable binary version that will run on your computer you must decode it by typing:
uudecode ruby1.uu
UNIX allows you to run as many programs concurrently as you wish. At any time, you can have one program running in foreground with which you can interact, and any number of others running in background.
Unlike some operating systems (e.g. Microsoft Windows), UNIX gives each active program its fair slice of processor time whether it be in foreground or background. Processor time is doled out to each program in turn by the operating system. UNIX does not depend on each program obediently returning control every so often to let its neighbours have a go.
Programs are therefore written as simple single-task processes which are run, interrupted, then continued according to a regular cycle.
Interactive programs like editors are simply parked in a frozen state when in background. This is simply because they are not receiving any stimulus from their only input source, the console keyboard, when they are in background mode. Programs which respond to events from sources other than the console carry on running as normal in background mode.
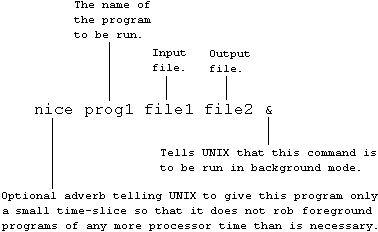
To launch a program in background mode, you type your command with an & at the end:
Changing Mode
If you have started a program in foreground and want to stop it, then switch it to background, or re-start it in foreground later, you type the following:
Ctrl-Z | to stop the current foreground program
|
|---|
fg | to re-start it in foreground again
|
|---|
bg | to re-start it in background mode
|
|---|
Job Control
Programs running in background are referred to as jobs. A single job can be made up of many processes, eg:
To find out what jobs are running in background, type:
jobs
[1] - Stopped (signal) elm
[2] + Stopped edit file1
[3] - Running prog1 file2 file3
The + indicates the job that was most recently-started or stopped.
bg %job | restarts the job in background
|
|---|
fg %job | restarts the job in foreground (the fg not necessary)
|
|---|
kill %job | kills the job completely
|
|---|
For the word job you can substitute one of the following:
- the job number shown in []
- enough of the the program name (eg
elm) to identify it uniquely
- % to refer to the most recently started/stopped job (type %%)
Background Programs and the Terminal
A background program cannot read from the keyboard. If it needs to do so, it stops. Its status is shown as follows:
jobs
[1] - Stopped (tty input) elm
Your options in this case are to type:
%% | to pull it into foreground
|
|---|
kill %% | to get rid of it
|
|---|
Full-screen programs are designed to save the screen when they are stopped and re-draw it when they are re-started.
To prevent or allow a background program overwriting the screen, type:
stty tostop | to stop background programs writing to screen
|
|---|
stty -tostop | to enable them to write to the screen.
|
|---|
UNIX commands that let you do things you are used to being able to do in DOS.
df | tells you how much free space is on the disks
|
du | tell you how much space your files are using
|
|---|
clear | clears the screen
|
|---|
touch file1 | changes date and time of file to now.
|
|---|
cat file1 file2 > file3 | puts the contents of the two files file1 and file2 into a single file, file3.
|
|---|
cp /docs/letter.wp . | copy to current directory
|
|---|
cp -r /home/ruby/* . | copy all files to current directory
|
|---|
od file1 | displays file1 in octal/hex/decimal/ASCII etc
|
|---|
ls | list names of files in current directory
|
|---|
ls -l | list full details of files
|
|---|
ls -x | do a multi-column listing of files
|
|---|
ls -a | list all files including hidden ones
|
|---|
ls -R | list files in sub-directories also
|
|---|
ls | more | list files a screen-full at a time
|
|---|
man ls | more | read manual about ls command a page at a time
|
|---|
help | get a menu of help information
|
|---|
echo $path | shows current settings of the path variable
|
|---|
rm -r dir1 | delete directory dir1 and everything in it
|
|---|
rm -ir dir1 | checks with you Y/N for each file in dir1
|
|---|
To find out what users (including yourself) are currently logged in to your UNIX computer.
who
root console 09:50:34 24 Jul 1995
rob vt01 13:14:45 21 Jul 1995
ruby vt02 16:34:23 21 Jul 1995
There is a line entry for each terminal. Each window on a workstation screen is regarded as a separate terminal. You can find out who is logged in to a particular terminal by typing:
who am i
rob vt01 13:14:45 21 Jul 1995
You get just the line pertaining to the terminal concerned. You can get a more detailed report by using:
finger
finger
Login Name TTY Idle When Location
root Admin con 1:11 Tue 20:16 lab
rob R J Morton vt 1:11 Mon 15:19 study
ruby R E E Morton vt 1:35 Tue 16:47 conf rm
You can also finger an individual as follows:
finger lisa
finger lisa
Login name: lisa In real life: Miss E R Morton
Directory: /home/lisa Shell: /bin/sh
On since 16:36 Tue 21 Jul 1995 on vt03 1 hour 27 minutes Idle Time
Project: Working on History Essay: Science in 17th Century England
Plan: To get degree in English with History and then go into
investigative journalism.
Project text is kept in a file called .project and the Plan text is kept in a file called .plan file. Both these files are kept in the user's home directory and are hidden files.
Who's on The Network
You can also find out who is on other computers on the network using finger as follows:
finger @tracy
where tracy is another computer on your network. You can also ask for details of individuals currently logged on to other computers:
finger jim@sharon
You can also use the rwho command. This compiles a list of everybody who is currently logged in throughout the whole network.
Quick Messages
You can send a short one-way message to another user as follows:
write jim
Phone me on 651697. Rob
Ctrl-D
Jim receives the following message on his screen:
Message from rob on eustace (ttyp1) [10:15 Wed 6 Jan 1995]
Phone me on 651697. Rob
<EOT>
Use finger to see which of your target's windows is currently active. Then send the message to that window:
write jim ttyp1
You can make your conversation two-way by substituting talk for write. The other user first gets the following message:
Message from Talk_Daemon@sharon at 10:15
talk: connection requested by rob@eustace
talk: respond with: talk rob@eustace
Park whatever program you are in with Ctrl-Z. Then type the response. The talk program then splits the screen into two separate send and receive windows.
To broadcast a message to every other user on your computer, type:
wall
Fire! Everybody out of the building immediately.
Ctrl-D
When you log in you may get a message:
You have mail.
You can then type the command:
mail
[First unread email message]
Your mailbox is a file called by your user name which is kept in a central mail directory called mail. Its path is:
/usr/mail/rob
This is quite separate from your mail sub-directory within your home directory:
/home/rob/mail
which you will use to originate email you wish to send or classify by sender and subject the email messages you have received. Individual messages within your mailbox file are separated by a row of 4 smilies (Ctrl-A) characters on a line by themselves. Your email address is always written in the form:
username@hostname
To read and send email you use an email program like mail, Mail, elm, pine. If you use Xwindows you can use MailTool or xmail.
Sending a Message
To send a message, you type-in the following command
mail user@host
Hello user, this is my message to you. What do you think
of it? I think it is great.
.
The dot on the line by itself at the end tells mail to go ahead and send the message. Old versions of mail may also need Ctrl-D.
Reading Your Mailbox
To get a list of outstanding incoming mail messages type the command:
mail
3 letters found in /usr/rob/mail.
0 scheduled for deletion.
0 newly arrived
> 1 234 jim@sharon 10:15:57 Tue 23 Jan 1995
3 56321 jack@plato 12:32:44 Tue 23 Jan 1995
2 4376 jill@ulysses 13:45:32 Tue 32 Jan 1995
?
You can then respond with the following commands:
Enter read the message the > is pointing at
Msg No moves the > to that message
d delete the message the > is pointing to
u undelete the message the > is pointing to
m followed by username@hostname to forward the message
r to reply to the message the > is pointing at
z to see next screen-full of message headers
p print the message the > is pointing at
q quit the mail program
? for further help, including other commands you can use
Reading a Message
Move the > to the message you want to read by entering its number and press Enter. The message is displayed. When you have finished reading it you can:
d delete the message
r reply to it with another email message
p 3 print message 3 on screen
s file1 save the message to the text file file1.
If file1 already exists, mail appends the new message to it. If you do not delete or save a message once you have read it, it is saved automatically in a file called mbox presumably in your own mail sub-directory.
Elm - a much better Email Program
To invoke the elm email program, just type:
elm
Mail box is '/usr/mail/rob' with 3 messages
1 22 Dec R J Morton (49) a few technical hints
O 2 23 Dec F Bloggs (12) memory upgrades list
N 3 23 Dec M Brean (10) new program notes
The following controls are in effect when you are in the mail index:
Up/Dn arrows move highlight to the message you want
Enter read the highlighted message
d delete the message after you have read it
u undelete the message
m send (mail) the message
r reply to the message
f forward the message to someone else
> s save the message to a folder or text file
p print the message
q quit the elm program
? for more help information and commands
o to go to elm's configuration options
h edit the header of the selected message
c go to a folder index to see the messages that you have
stored in a particular sender or subject folder.
When you press m, elm asks you for:
- the address to send it to
- the subject of the message
- the addresses to send copies to
Elm then it runs an external text editor for you to type the message you wish to send. Then save it and exit the editor. You may then if you wish press h to edit the message's header information. Elm then gives you the following choices:
Choose e)dit message, !)shell, h)eaders, c)opy file, s)end, f)orget.
You can then press s to send it.
You set up which text editor you want elm to use as follows:
- press o to get the elm options
- press e to change the editor
- type the name of the editor you wish to use
- press > to save the change
- press i to get back to the mail index
To read a message, you highlight its line and press enter. Elm prints (on screen) the first screen-full of the message. After you have read it, you can press:
d to delete the message
f to forward it to somebody else
r to reply to it
space to leave it in the mailbox and go to the next message
i to leave it and go back to the index
> s to save message to a folder
When saving to a folder, elm asks the file name of the folder. Folder names begin with an '=' sign.
Folders can be named after the people you receive the messages from, or by the subjects of the messages.
You can look at the messages you have saved in a folder by pressing c while in the main index. You then type in the folder name and a list is displayed of all the messages currently in that folder. You look at folder messages the same way you look at them in the mailbox.
If you do not use an '=' prefix, elm assumes you are saving to an ordinary text file. The text file may be imported into a document if required.
With UNIX, all the disk storage on a given computer is organised into a single inverted tree directory structure. The top directory, which contains all other subdirectories and files, is called the root and is represented by a /. The root directory is based on the machine's first disk drive. It is divided into sub-directories.
The user sees this directory structure as the neat seamless tree, but in fact, it may be spread over several disks on his own workstation, plus some storage on a host connected via the local area network. The df command produces a report that reveals the physical disks on which the various sub-directories are really stored:
df
File System Mount Point
/dev/sd0a /
/dev/sd0g /usr
/dev/sd0h /home
/dev/sd3a /tmp
eustace:/usr/spool/mail /var/spool/mail
eustace:/usr/spool/news /var/spool/news
eustace:/usr/lib/news /var/lib/news
This says that the user's root directory is on the workstation's own disk sd0a, his usr sub-directory is on disk sd0g, his home directory is on disk sd0f and his tmp directory is on drive sd3a. In NFS terms, sub-directory /usr is said to be the mount point for disk sd0g, /home is said to be the mount point for disk sd0f and /tmp is said to be the mount point for disk sd3a. The local directory structure with the mounting points of the various local disks is shown below:

Sub-directory mail under the local parent sub-directories /var/spool is located on another machine on the network whose name is eustace. The same is true for the news sub-directories under their parent sub-directories /usr/spool and /usr/lib respectively. Eustace's directory /usr/spool/mail is said to be mounted at sharon's directory /usr/spool/mail and similarly for /usr/spool/news and /usr/lib/news.
NFS is susceptible to other machines crashing and being re-started. It cannot handle the simultaneous updating of files by different users very well. It cannot handle server crashes. Other remote file systems are RFS, AFS and Novell Netware.
telnet
Telnet is a UNIX service which connects you to the command line of a remote computer over the network. It is as if you are on a terminal connected directly to the remote machine. Below is a typical telnet session in which your local machine is called sharon, and the remote machine you are connecting to is called eustace:
telnet eustace
Trying...
Connected to eustace.ebs.co.uk
Escape character is '^]'. SunOS UNIX on eustace.ebs.co.uk
login: rob
Password:
Last login: Thu 7 Jan 1995 from sharon
SunOS Release 4.1.2 (EUSTACE) #3 at 22:44 Fri 16 Oct 1994
Please confirm or change your terminal type.
TERM=(ansii)
...............
...............
...............
...............
logout
Bye Bye
Connection closed by remote host.
Then you are back at the command prompt on your own machine. If the remote host freezes up on you and does not respond to the logout command, you get the attention of your local telnet daemon by typing the escape character Ctrl-]. You then get the local telnet prompt and type quit as follows:
telnet >quit
Your local telnet daemon then disconnects you from the remote host. Telnet can log you in to non-UNIX machines. In this case you will be talking to whatever operating system that remote machine uses.
rlogin
UNIX has a remote login utility called 'rlogin' which also allows you to log in to remote machines, but they must be UNIX machines. Below is a typical rlogin session:
rlogin eustace
Last login: Thu 7 Jan 1995 from sharon
SunOS Release 4.1.2 (EUSTACE) #3 at 22:44 Fri 16 Oct 1994
Please confirm or change your terminal type.
TERM=(xterm)
...............
...............
...............
...............
~.
If used within a network of UNIX machines with a common NIS (network information system), 'rlogin' does not need to ask for your user name and password because it enables the remote machine to know that all users of your machine are allowed to use it too. Each machine in the NIS group has a file called /etc/hosts.equiv in which is stored a list of the names of all machines it can trust to have the same set of user names and passwords.
If the remote UNIX machine is not part of your machine's NIS group, it asks you for your user name and password just as telnet does. However, you can have your own file '.rhosts' in your home directory which contains a private list of trusted machines, e.g.:
eustace robby
sharon rob
tracy rob
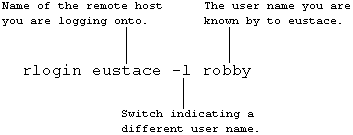
To eustace I am known as 'robby' while sharon and tracy know me as 'rob'.
You can log in manually to a machine on which you have a different user name as follows:
cu
Stands for 'Call UNIX'. Enables you to dial-in to a remote UNIX host using a modem. It can dial in to non-UNIX machines and is used to gain access to email services like CompuServe.
cu 01279554321 | expedites a dial-up call to a remote host
|
|---|
cu eustace | if host name is written into the cu data file
|
|---|
~. | to terminate the call
|
|---|
rsh
Stands for 'remote shell'. Enables you to execute one command at a time on a remote UNIX host.
rsh eustace lpq shows what is waiting on eustace's print queue
It uses the same user name & password strategy as 'rlogin'. You cannot execute full-screen programs with 'rsh'.
rcp
Stands for 'remote copy'. Its use is illustrated by the following examples:
rcp eustace:file1 eufile1 | copy from eustace
|
|---|
rcp eufile2 eustace:file2 | copy to eustace
|
|---|
rcp eustace:~ruby/file3 eufile3 | copy from another user on eustace
|
|---|
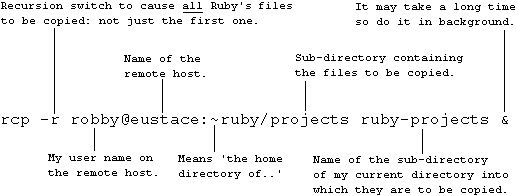
The following copies all the files in my local project directory to my projects directory on eustace, and then confirms that the files got there by using the 'rsh' command to list all the files in my projects directory on eustace.
rcp -r projectdir eustace:projects
rsh eustace ls -l projects
ftp
Stands for 'File Transfer Protocol'. It works with non-UNIX hosts. A typical FTP session follows:
ftp eustace
Connected to eustace.ebs.co.uk
220 eustace.ebs.co.uk FTP server (SunOS 4.1) ready.
Name(eustace:robby):
331 Password required for robby.
Password:
230 User robby logged in.
ftp>quit
221 Goodbye.
You can log on to various public service machines as an anonymous user. In this case you enter your user name as 'anonymous' and put your email address as your password.
Ctrl-C aborts current ftp operation and gets back the ftp prompt.
ftp> dir lists directory on remote computer (invokes ls -l)
ftp> hash displays a # for every 1000 characters transferred
ftp> get file1 eustace-file1 copy eustace's file1 to local file
ftp> put eustace-file1 file1 do the reverse
ftp> cd mail change directory
250 CWD command successful
ftp> pwd display working directory id
257 "/mnt/users/rob/mail" is current directory.
ftp> mget * multi-file get
ftp> mput * multi-file put
ftp> binary transfer files in binary mode
ftp> text transfers files in text mode
For a fuller explanation of ftp commands see the Internet notes on FTP.
rm file1 file2 dir1/file1 deletes the specified files
rm *.bak deletes all '.bak' files in current dir
rm -i * query each file Y/N as you delete them
rm * .bak deletes all files in current directory
then tries to delete the non-existent
'.bak' files
rm sec*tx deletes all files whose names start
with sec and end with tx.
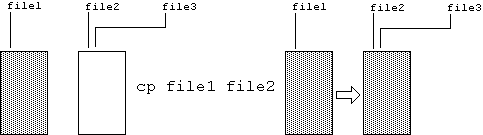
The command cp file1 file2 copies contents of file1 into file2. Both file1 and file2 then contain duplicates of the same information. The original contents of file2 (if any) get blown away. If file2 had another name (file3), then file3 also now refers to the new contents.
The command mv file1 file2 severs the file name 'file2' from its original contents and connects it to the contents of the file called 'file1'. The original contents (shaded) can then be referred to by either file name. If the original 'file2' was linked to another file name 'file3' they can still be referred to by the linked name 'file3':

The command ln file1 file2 causes the file name 'file2' to disconnect from the data it originally represented and connect to the same data as the file name 'file1':

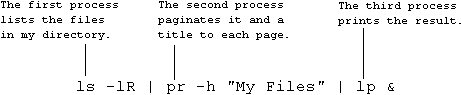
A process is an instance of a running program such as the 'lp' program printing a file called file1. Where a command has been entered which specifies a sequence of programs such as:
ls -lR | pr -h"My Program" | lp &
the whole thing is regarded as a single process comprising programs 'ls', 'pr' and 'lp' running in sequence.
Process Status - System V
The System V version of the ps (process status) command displays information about processes that are currently active within your computer. The straight forward ps command produces the following listing:

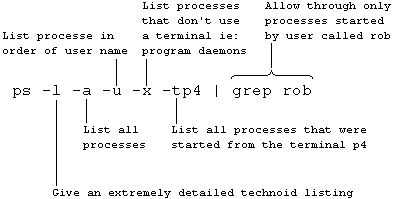
The System V ps command can take certain switches:

The full or detailed (-f) listing produced by System V is:
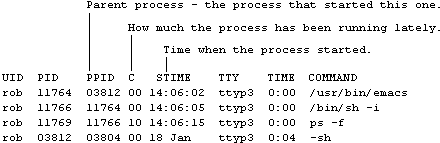
Process Status - Berkeley
The Berkeley version of ps produces the following basic listing:
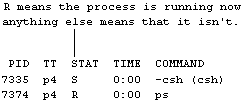
The switches applicable to the Berkeley version are:
The detailed (or user-oriented) listing produced by the Berkeley version is:
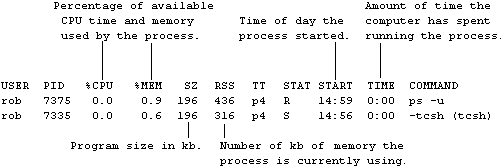
Note the difference in the meanings of the -u switch between System V and Berkeley. In System V it gives you a listing pertaining to a named user. In Berkeley it invokes the full listing which is listed in user-order rather than process order.
Note that cd is not a process. If you change directory while in a child process, the change is still in effect when you return to the parent process. Real processes cannot affect their parents.
Aborting a Process
To abort the running foreground process:
Ctrl-C or Del aborts the process immediately
and returns to shell.
But some programs intercept Ctrl-C because it is a valid command to the program. To abort such programs try:
Ctrl-\ halts the process, saves its
current memory image in a file
called core, clears the dead body
of the process from memory, then
returns to the shell.
Ctrl-Z freezes the process intact
and returns to the shell
To kill the frozen (halted) process you must go to another terminal or window, use the ps command to find out the process's PID, then:
kill 24806 asks Process N° 24806 to terminate itself
kill -9 24806 tells UNIX to forcibly terminate Process
N° 24806
To release a Locked-up Terminal type 'Ctrl-J' then 'stty sane' followed by another 'Ctrl-J'. If Xwindows locks up the whole screen, go to another terminal, use 'ps' to find the 'PID' of the Xwindows process which is called 'Xgp', then type 'kill -9 nnnnn', where 'nnnnn' is the 'PID' of 'Xgp'. If you are using Motif or Open Look, the process to kill is the one with :0 (that's colon-zero) after its name. Another way of knowing which process is the GUI is that it is by far the most greedy process alive as regards its consumption of CPU time.
Common Error Messages
No such file or directory
Arg list too long
Broken pipe
Cannot access No such file or directory
Cross-device link Different file system
Device or resource busy
Different file system [ln your system cannot do soft links]
File exists [a file of that name already exists]
File table overflow [too many files open at once]
File too large [each user is set a maximum file size]
Illegal option [an invalid switch has been used]
Insufficient arguments
I/O error
Is a directory [you're treating a directory as a file]
Login incorrect
No process can be found
No such process
No more processes Can't handle any more processes at present
No such file or directory
No space left on device [disk full etc]
Not a directory
Not enough space [in memory or on disk]
RE error UNIX cannot understand your regular expression
Read-only file system
Too many links You've made too many links to a file
Usage You've used incorrect syntax in command
444 mode You don't have permission to delete named file
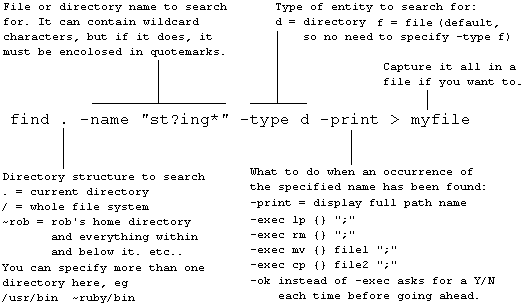
The find command allows you to search for lost files and directories by name. Given a file or directory name (which may contain wildcard characters), it produces a list of the full path names for every match it finds:
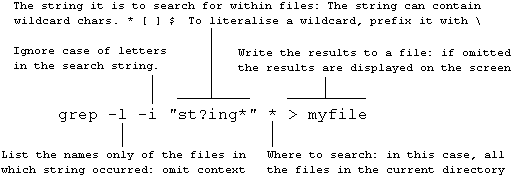
The grep (global search for regular expression and print) command searches the contents of files for the occurrence of a given string. The string may contain wildcard characters.
You can link a new file name 'file2' in your current directory to an existing file called 'file1' by using the 'ln' command:
ln path1/file1 file2
You can rename a link name with 'mv' and delete a link with 'rm' the same way as for a real file name. If you made a soft (using the -s switch) link to another file system which the owner subsequently deletes, you are left with a dangling link which you can't access. Just delete it.
The information line produced when you enter the command 'ls -l file1' is shown below:
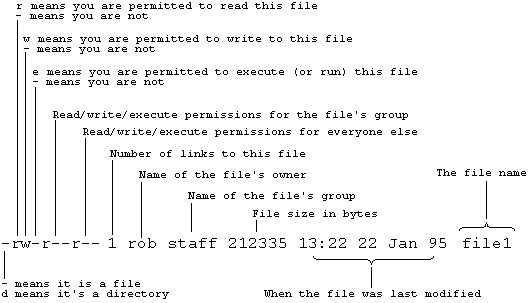
For a directory, e-permission allows you to cd to the directory and open files within it.
The three sets of permissions for a given file or directory are held in three 3-bit sets:
000 0 No permission
001 1 Execute-only (useful for safeguarding software)
010 2 Write-only
011 3 Write and execute allowed
100 4 Read-only
101 5 Read and execute allowed
110 6 Read and write allowed
111 7 Read, write and execute all allowed
On some systems they are displayed as the three corresponding octal digits:
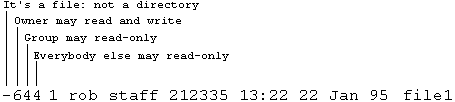
Groups are sets of people with the same permissions. To see which group you are in, enter the command 'id'. You can be a member of more than one group. To see who is in your group, enter "grep 'grpup-name-here' /etc/group".
Changing Permissions
You can change the permissions for files you own. The most straight-forward way is to specify the three absolute permissions in octal as follows:
chmod 660 file1
There is what is supposedly a more user-friendly way of changing the read / write / execute permissions using letters:
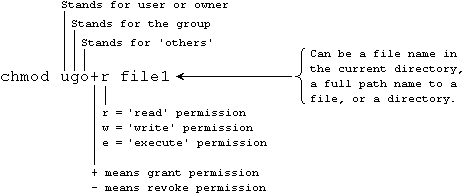
Changing Ownership
You can transfer the ownership of one of your files to someone else as follows:
chown ruby file1
But you must be the owner of the file in the first place.
If someone copies a file that they own into your home directory, they still own it unless or until they transfer its ownership over to you.
If you copy one of their files (assuming the existing permissions allow) into your home directory, they still own the original, but you own the copy automatically.
Changing Group
You can also — as the owner of a file — change the group that can use it. To do this, enter something like::
chgrp workers file1
Your login script is stored in a file in your home directory called:
.login for the C shell
.profile for the Bourne & Korn shells
This file contains shell commands which are run automatically every time you log in. The C shell also has a file called '.cshrc' which is run automatically every time you start another shell with the 'csh' command. A typical login file could contain the following commands:
set path=($path ~/bin) show UNIX where to look for programs
set ignoreeof tell C-shell not to exit on Ctrl-D
stty erase '^?' kill '^X' change terminal control characters
stty -tostop allow background programs to write to screen
mail check for new email messages
cd favorite.directory change to directory to start in
You can also change the shell prompt. The standard terminal control characters are:
Ctrl
erase H Erases (backspaces over) previous character
kill U Discards the line typed so far
eof D Marks the end of input to a program
swtch Z Pauses the current foreground program
intr C Interrupts or kills current foreground program
quit \ Kills the program and writes a core file
uucp is to UNIX systems what Kermit or Zmodem is to PCs. uucp stands for UNIX-to-UNIX copy. uucp is a dial-up modem-to-modem file transfer program. Usage of the uucp command is as follows:
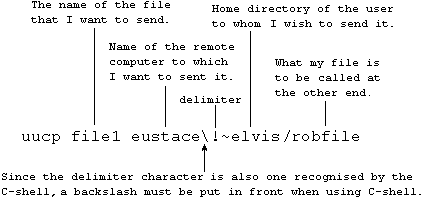
For copying a remote file to your machine, reverse the order of the two arguments.
Popular CPU chips
80286 intel 16 Mediocre CISC
80386 intel 32 Mediocre CISC
80486 intel 32 Fast CISC
Pentium intel 32/64 Really Fast CISC
860 intel 32 Fast RISC
68020 Motorola 32 Mediocre CISC
68030 Motorola 32 Fast CISC
68040 Motorola 32 Faster CISC
88000 Motorola 32 Faster RISC
88100 Motorola 32 Even Faster RISC
R2000 MIPS 32 Fast RISC
R3000 MIPS 32 Faster RISC
R4000 MIPS 32 Really Fast RISC
Microvax DEC 32 Varies CISC
Alpha DEC 64 Extremely Fast RISC
Precision HP 32/64 Extremely Fast RISC
RT PC IBM 32 Mediocre RISC
RS/6000 IBM 32 Fast RISC
SPARC Sun/Others 32 Mediocre to Fast RISC
CISC = Complex Instruction Set Computer - old & slow.
RISC = Reduced Instruction Set Computer - new and fast.
16 bit machines can address 65,536 bytes of memory.
32 bit machines can address 4,294,967,296 bytes of memory.
Immediate Memory
UNIX used to run in 50k of memory
UNIX now needs about 2MB of memory.
UNIX workstations usually have about 100MB of RAM.
UNIX hosts can have up to 1000MB of RAM.
PCs usually have a maximum of 4 to 8MB of RAM.
Virtual Memory
UNIX uses virtual memory. Programs are divided into 4k pages. Only the most recently used pages are kept in RAM. If a part of a program is called which is not currently in RAM, it is loaded into a spare page and then executed. It can make programs a lot slower than if they can be fully accommodated in RAM all at once.
Disks
Minifloppy rw 5¼" 300k to 1.2M
Microfloppy rw 3½" 400k to 4M
CD-ROM r- 5¼" 600M
Magneto-optical rw 5¼" 600M or more
Tapes rw -- 20MB to 2GB
"Blue Suede Shoes" requires a 5M digital audio file.
A 32-bit machine can directly address 7 CDs-worth of data.
SCSI (scuzzy) Disk/tape drive interface standard.
Screens: Range from 12 to 20 inch. Generally, the bigger the better. Size is becoming more important as the use of GUIs increases. Colour screens are more fun, but monochromatic screens are generally better for serious work.
Keyboard: UNIX software has always had to anticipate being used with a variety of different keyboards. But get one with function and arrow keys.
Mouse: UNIX systems were designed for the 3-button mouse.
GUI - Graphical User Interface
Originated from the Xerox Park project around 1975. Most UNIX systems have GUIs based on Xwindows. Advantages of Xwindows are:
it runs on all sorts of computers - not just UNIX
its screen layouts and styles are not constrained
uses a networked client-server architecture
it's free via the Internet from MIT
Although basic Xwindows is free, you will need to adapt and recompile the code for your particular screen-type.
The work of determining what appears on the screen is divided between three different programs as follows:
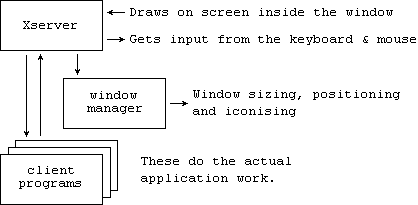
You can do the following to the windows on your screen:
Change their layering: which window is at the front.
Move them around
Change their sizes
Reduce them to icons and vice versa
Everyday Commands
cat lists a text file
cd change directory
cp copy a file
find finds where a named file is
grep finds which files contain a given string
ln link a new extra name to an existing file
lp lpr print a file
lpstat lpq show the status of the print queue
ls list a directory
mkdir make a directory
more show screen output a screen-full at a time
mv move or rename a file
pwd tell current working directory
rm erase a file
rmdir remove a directory
Frequent Commands
bg re-start a stopped process in background
clear clear the screen
dircmp compares the contents of two directories
emacs text editor program
exit log out
fg re-start a stopped process in foreground
kill kill a process, given its PID
man display what the manual says about a given command
passwd change your password
pr put page titles and numbers on a text file printout
ps process status
Occasional Commands
cancel cancels a print job
chmod change permissions for a given file
cmp compare the contents of two files
compress compress a given file
csh start the C shell
df shows amount of free space on disk
diff compares two files (bdiff & sdiff)
du shows how much space your files take up on disk
echo puts messages and prompts on screen in scripts
help
glossary
id tells you which group you are in
jobs lists all your jobs (foreground & background)
mesg sets whether or not others can write to you
sort sort lines of a text file into order
stty set terminal control chars and background write
tty identify the terminal you are on
uniq remove all duplicated lines in a text file
Useful Commands
at set given programs to be started at a given time
bc invoke a nerdy formula evaluator program
cal prints a calendar for given month or year
date show system date and time
diff3 compares 3 files
finger identifies other users currently logged in
head reads the first 10 lines of a text file
history Lists the last 20 or so commands you typed
news Lets you read administrator's news items
script saves commands and responses in a script file
sdiff compares two files by listing them side-by-side
spell checks a text file for spelling
sum computes the checksum of a file
tail displays the last 10 lines of a file
talk enables two-way split-screen typing
tee copies from keyboard to screen and a file
time tells you how long a command took to run
uname tells name of UNIX system you are on
wc number of words -w, lines -l, chars -c in a file
who lists who else is currently logged in
who am i says who is logged in on this terminal
Seldom Used Commands
ed all the old largely disused text editors
red
vi
ex
Commands for Experts
ar creates an archive file of several files
batch enter a bunch of commands to run later
awk programming language
chgrp change the group able to access a named file
chown transfer ownership of named file to another user
cpio copy to and from tape
crontab programs to be run at the same time every day
cut cut a given column out of a tabulated text file
env shows current user environment variables
file is it a file, a directory, or something else
ksh run the Korn shell
login logs you in as someone else
nice run program in background with small time-slice
nohup run program in background while logged out
od displays a file in ASCII, octal, hex etc.
rlogin log in on a remote computer
rn reader for usenet news
rsh run given command on a remote computer
sed uses pre-recorded commands on ed
set shows which environment variables are in effect
setenv sets environment variables
sh runs the Bourne shell
tar copies files to and from backup tapes
telnet log in to a remote (possibly non-UNIX) machine
touch reset a file's time/date to current time/date
tr replaces all occurrences of a char with another
troff text formatter
umask default permissions to give your files
unset removes the environment variable
uucp Kermit-type file transfer utility
xargs repeatedly executes a command for each of a list
of arguments or file names.
Shell Script Commands
basename gets last item in a path spec (usually a file name)
dirname gives name of directory that contains given file
export make immediately effective changes to a script
read accepts a line of text from user during execution
sleep wait given number of minutes
test test to see if a condition is true or false
Achaic Commands
alias establishes alternative names for commands
fmt old text formatter
pg old version of more
unalias undoes aliases
© 1998 Robert John Morton
![]() My Software
My Software